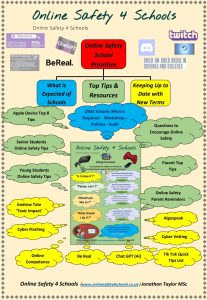
The vile, illegal and hurtful online crime that is ‘Sextortion’ has been used to bully harass and extort many young people and would often start out with teenagers acting silly in front of a camera sending each other flirty sexy texts and pictures but should the friendship or relationship break down then the same images could be used to exploit, upset and humiliate.
Definition

Sextortion, a combination of “sex” and “extortion,” refers to a form of blackmail where sexual information or images are used to extort money or other benefits from the victim. Whilst sextortion is seen as a modern crime due to the digital age, has roots that can be traced back to earlier forms of blackmail.
Sextortion has transformed from traditional forms of blackmail to a complex and pervasive issue in the digital age. The increasing sophistication of technology continues to pose challenges in combating this form of exploitation, necessitating ongoing legal, social, and technological efforts to protect potential victims and hold perpetrators accountable.
Teenagers and Young Adults: Studies have shown that teenagers and young adults are particularly vulnerable to sextortion, often due to their high engagement with social media and dating apps.
Is Sextortion New ?
Before the advent of the internet, sextortion primarily involved physical letters, photographs, or coercive sexual acts. During the Cold War, intelligence agencies would use compromising photographs to blackmail individuals into providing information or conducting espionage activities. Known as “honey traps,” these tactics often involved seduction and subsequent blackmail. Hollywood in the mid-20th century saw various forms of sextortion where private photographs or information about illicit affairs were used to manipulate celebrities or extort money from them.
Emergence of Social Media and Online Games: The rise of the internet and more importantly the use of Social Media, Online Games in the late 20th century significantly altered the landscape of sextortion:
Email and Online Messaging: As early as the 1990s, with the widespread use of email and instant messaging, perpetrators began exploiting these platforms to threaten victims with the release of compromising photos or videos.
Webcams and Cybersex: The early 2000s saw the explosion of webcams, which facilitated a new form of sextortion where victims were coerced into performing sexual acts on camera, only to be blackmailed with recordings of those acts.
Technological Advancements
With the advancement of technology, sextortion has evolved into a more sophisticated and widespread threat:
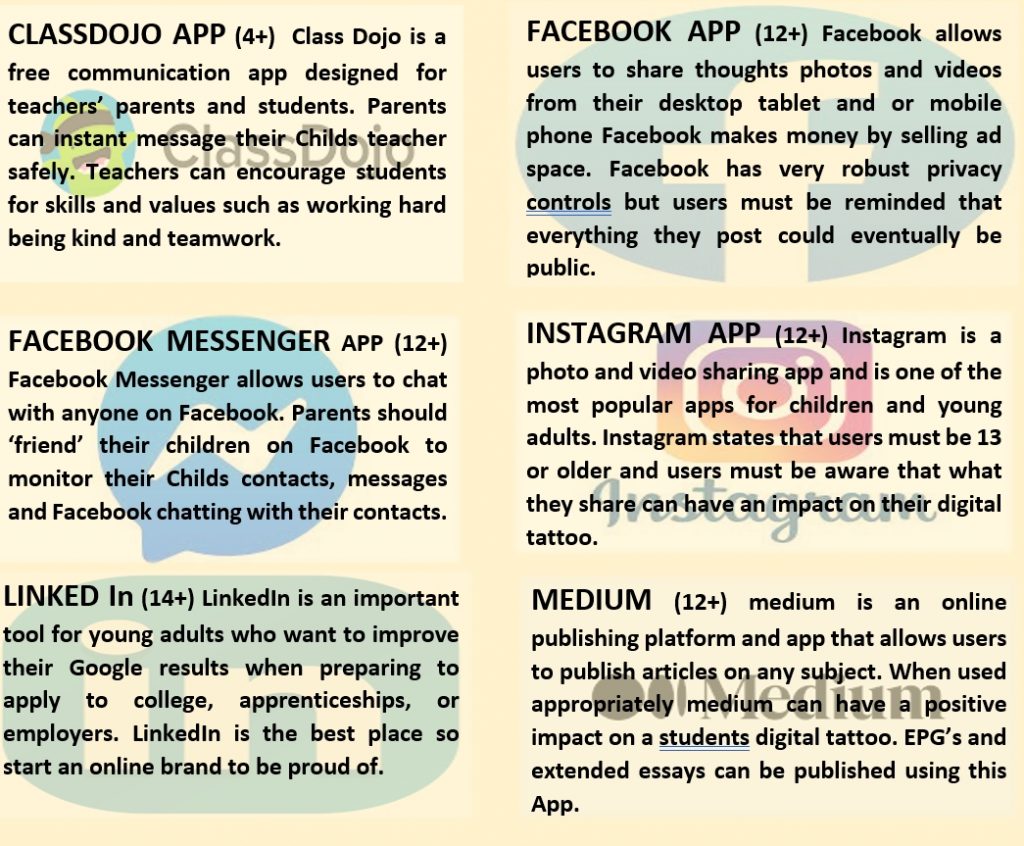
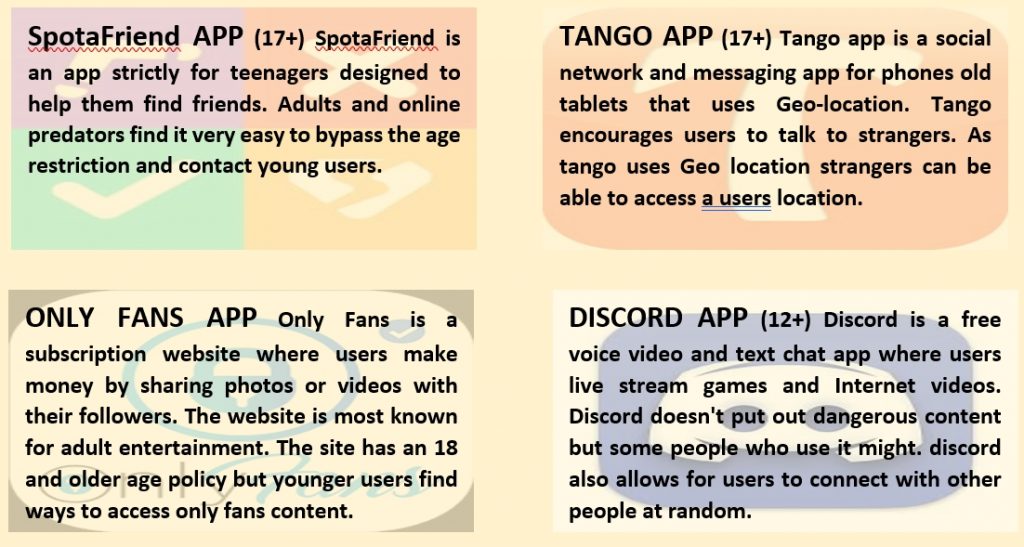
Social Media and Dating Apps: Platforms like Facebook, Instagram, Snapchat, Tik Tok and various dating apps have become common venues for sextortion. Perpetrators create fake profiles to lure victims into sharing intimate images or videos.
Online Games: Fortnight, Roblox and Minecraft have also become venues for meeting victims of sextortion. Contact and messaging victims to allow for viruses to infect devices and retrieve personal information can occur through the platforms messaging service.
Ransomware and Malware: Cybercriminals deploy malware to gain access to victims’ personal devices, obtaining private data and images to use for extortion.
Deep Fakes: The advent of Deep Fake technology, which allows for the creation of realistic but fake videos, has introduced new dangers in the realm of sextortion. Perpetrators can fabricate compromising videos, images and headshots and use them to extort victims.
Legal and Social Responses : In response to the rise of sextortion, legal systems and advocacy groups have taken various steps:
Legislation: Many countries have introduced specific laws to combat sextortion, recognising it as a distinct criminal offense. Penalties for perpetrators have become increasingly severe.
Awareness Campaigns: NGO’s and law enforcement agencies have launched awareness campaigns to educate the public about the risks of sextortion and how to protect oneself.
Support Systems: Victim support systems, including hotlines and counselling services, have been established to help those affected by sextortion.
Sextortion Update 2024 – 2025
The US National Centre for Missing and Exploited Children reported a more than 100% increase in sextortion cases from 2022-23 – rising to 26,718 from 10,731. Furthermore, while both sexes and all age groups were targeted, a large proportion of cases involved male victims aged between 14 and 18. All age groups and genders are being targeted, but a large proportion of cases have involved male victims aged between 14-18 (91% of victims in UK 2023 were male.
Sextortion is now perpetrated by Organised Crime Groups (OCG’s) based overseas, predominantly in some West African countries, but some are also known to be located in Southeast Asia.
Victimology & Methodology – Typically, boys are extorted for MONEY, Girls are extorted for MORE IMAGES.
Perpetrator known to Victim – Spurned or rejected boyfriends who in their bitterness or desperation used threats to punish former lovers or coerce them back into relationships. These men stalked, harassed, and badgered their former partners in ways that could be terrifying and overwhelming. Furthermore, malicious seducers, used friendship, deception and promises of romance to acquire compromising pictures from targets they met online, and then used these pictures to extract more images and sex. The personal and psychological toll on victims was intense, with almost one-quarter seeking medical or mental health assistance and 12 percent moving from their homes as a result.
Unknown Online Perpetrator Callous sextorters, usually disguising themselves as ‘young and attractive’ women will often follow a young person’s social media accounts or send them friend requests’ pretending to be a ‘young and attractive’ woman. They will usually try and identify with the victim through private messages, such as mentioning they are studying at a particular university and school. The conversation can last for days before it takes a dark turn.
Sextorters will gain their trust and attempt to progress things to the next level, often sending intimate pictures of the person they think they are talking to, encouraging them to do the same. However, once they have an intimate picture or video of the victim, they will immediately use this material against them. A typical message will say: ‘Stay calm, don’t panic, I have recorded that video / saved that picture of you and I will ruin your life if you don’t follow my instructions.’ They will then send a screen grab of all the victim’s social media contacts such as friends, family and colleagues and threaten to send it to all of them unless they are paid. They will even attempt to call the victim to heighten the threat. On most occasions, the voice is that of a male and not a female.
OCG’s (Organised Crime Groups) using Ai (Artificial Intelligence) Deep Fakes involve videos, images, or audio recordings that look or sound completely realistic but have been altered using AI. Faces can be super-imposed, expressions can be manipulated, and separate elements can be combined to produce something entirely new. These are all hoaxes that are commonly used to show someone doing or saying something they did not do or say. Sexually explicit Deep Fakes are used to trick children into sending nudes or livestreaming sexual acts.
Methodology – Online Games like Fortnight, Roblox and Minecraft are mostly played by young boys, this could be the reason that we have seen a complete change in victims of Sextortion, and of course this type of sextortion involves sending money to the sextorter, but how?
V-Bucks are an in-game currency that can be spent in Fortnite. In-game purchases that can be made with V-Bucks include customization items like New Outfits, Gliders, Pickaxes, Emotes, and Wraps, or even the latest Battle pass!
Robux is the virtual currency used in Roblox gaming, players can earn or purchase Robux to buy in-game items, accessories, and other virtual assets.
Minecoin is the digital currency for Minecraft, which can be spent on avatar ‘skins’, new ‘textures’ for blocks or entire virtual worlds created by the game developers or other members of the Minecraft community.
Users / gamers of these games predominantly boys, and 9 – 16 year old boys find it necessary to have this online currency for more game enjoyment and online credibility, hence requiring a ‘Bank Card’ to facilitate payment
Online Payments: Approximately 50% of all the online gaming students (aged 9 – 16) I have spoken to admit to having a parents payment card readily available to use and are not quizzed as to what they are buying , many simply have weekly budgets of £50. This allows for extorted money to be paid, furthermore if the amount requested is £50 then absolutely no reason for parents to question the payment.
Malware Viruses: OCG’s use software and ‘Bots, to send thousand of notifications or requests to young gamers via Fortnight, Roblox and Minecraft, these contain ‘malware’ that allow for access to contact lists, personal information from the device they are using (their smart phone). This gives the OCG ‘Bot’ information to pressurise and extort money from the victims.
Bots: Computer bots can be used for the large-scale exploitation and demands (1,000s), allowing for a percentage of victims to simply ignore the threat, however a large number of victims will make the small financial payment. It makes sense for the OCG to make smaller demands (£50) because if many less resilient and vulnerable young children can make easy only payments due to fear, then hundreds pay, and the financial rewards are huge.
Images : Sextortion originally relied on the existence of real images or videos however, Deepfake sexually explicit images or videos that do not exist, but are created, are being used by the OCG’s as a result of personal data being retrieved as a result of viruses. There are 3 techniques.
In the 1st Technique, it is possible to replace the face of a naked person with that of another person, with the aim of creating a deepnude. This technique is called Face Swap.
The 2nd Technique is the Undress technology. This technology uses artificial intelligence to predict how a depicted person would look naked based on just one photo. In this case, no additional image is used for the manipulation, but the image of the person is the source material on which the artificial intelligence is programmed.
The 3rd Technique no longer starts from a specific image as the source material to create a new naked image, but trains through a huge quantity of images to create a completely virtual naked person.
Conclusion
Sextortion is not new, it has been used to exploit financially or sexually, shame, hurt, harass, or extort for many years, what has changed over time is the victimology and the methodology. As already stated, typically, boys are extorted for money, girls are extorted for more images. Whilst girls have been victims of sextortion since the use of the internet and social media began, we now see that young boys are being targeted because of technological advancements, namely Artificial Intelligence, malware and ‘Bots.’
Sextortion will continue to evolve, schools, parents and trusted adults must be aware of the different ways sextortion can occur and how their students or children can fall victim to bitter friends, online strangers, or Organised Crime Groups.
Advice and Tips
I do provide workshops, advice and tips for professionals, parents, and trusted adults, if anyone would like to receive training and advice, please do message or email.
onlinesafety4schools@gmail.com